If you’ve ever checked your Windows Experience Index, you might wonder whether you can increase these numbers without buying a new PC. Today we’re going to show you how to hack the WEI to show whatever numbers you want.
Why You Might Want To Do This
So you might be wondering why in the world would you want to do this, firstly the Windows Experience Index has an API that programs can use to enable functionality. This means that if your score is too low, some parts of a program may have dumbed down functionality or even be completely disabled. You could use this hack to trick your system into allowing you to use features. Additionally if you are really geeky, like we are, you can use it to cheat in a benchmark test against your friends.
Hacking The XML File
The first method, and the most fun, requires some knowledge of XML files, however if you follow this tutorial you will be fine. So lets get started.
You are going to have to navigate to C:\Windows\Performance\WinSAT\DataStore
Now you are going to need to open a file that ends with Formal.Assessment (Initial).WinSAT) if there is more than one file that ends with that name look at the date and the begining of the file and choose the most current one. Right click on the file and select edit, this will open it in notepad.
Click on the edit menu and then select find. When the find dialog box opens type <WinSPR>, and click find next.
Notepad will then highlight where the code that we need to edit starts. You can edit any values of the WEI, to see what tags edit what values see the blockquote below the image. All the tags that you will be looking for follow the WinSPR tag.
To Change One Of The Values Look For The Following:
<SystemScore> tags change the overall rating
<MemoryScore> tags change the Memory (RAM) rating
<CpuScore> tags chang the Processor rating
<GraphicsScore> tags change the Graphics rating
<GamingScore> tags change the Gaming Graphics rating
<DiskScore> tags change the Primary Hard Disk rating
For example if i wanted to change the value of my system score to 7.9 i would change the value between <ystemScore> and </SystemScore> to 7.9 as seen below.
Save the file on your desktop and dont rename it. Now cut the file from your desktop and paste it in C:\Windows\Performance\WinSAT\DataStore. You will be asked to provide Administrative credentials if you are not a Local Administrator, if you are then you will just need to click continue to provide access.
After you have pasted the file in the DataSore folder, go the the Windows Experience Index to see the changes.
The Alternative Method
The first method was a little advanced and required a little knowledge of XML, however if you are an ordinary end user there is still hope. As it would turn out, there is a small program that was designed to do all of this for you.
To use it you will have to download it (see the download link at the end of the article) and run the portable application, which will be called experience_index_editor.exe If you are making the download on a Windows 7 machine the download will be located in the Downloads folder.
You will need to either have Local Admin privileges or know the credentials of a Local Admin account to run the program.
Once the program has run, you will be presented with an easy to use interface, from here you can just change the values of your Windows Experience Index. Each text box changes a different score in the index. You can see what score it changes by looking at the field just before the text boxes. To change one of your scores just type a number between 1 and 7.9 in the box. You can change one or all of your index scores but remember that your overall system rating is taken from the lowest score.
Once you have made your changes click the save button. Close the program and go to the Windows Experience Index to see your changes immediately.
Reseting Your Score To True Values
To reset your Windows Experience Index to the true values, all you have to do is re-run the assessment. To do this go to Computer and click System Properties in the toolbar.
When the System Properties open. Click on the Windows Experience Index link.
The Windows Experience Index will now open, from here you can view your current WEI scores however from here you can also re-run the assessment by clicking on the link that says “Re-run the assessment”
You will need to either have Local Admin privileges or know the credentials of a Local Admin account to re-run the assessment.
Conclusion
Whether you are are just doing this for fun, or to enable functionality that you previously did not have, please remember that this will not actually increase your systems performance.
Download the WEI Editor from
here.












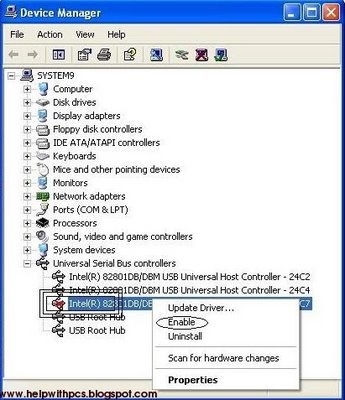
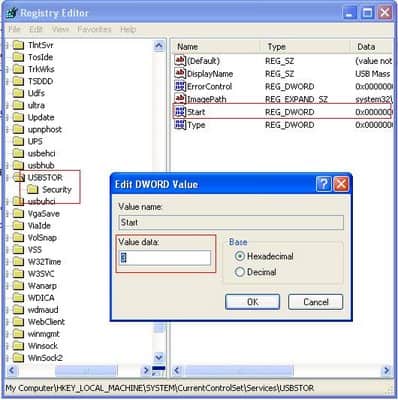
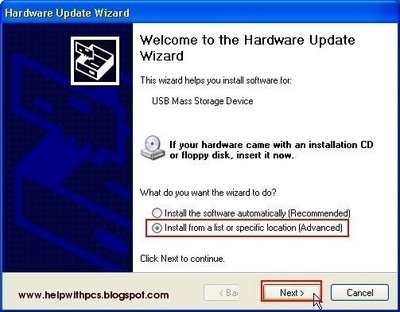


 Installing Windows from a USB flash drive has several advantages – First of all, the overall speed of the installation process will increase significantly, carrying a USB stick is much more convenient than a DVD, and finally it becomes possible to install the OS even on those systems that do not have a DVD drive, such as a netbook.
Installing Windows from a USB flash drive has several advantages – First of all, the overall speed of the installation process will increase significantly, carrying a USB stick is much more convenient than a DVD, and finally it becomes possible to install the OS even on those systems that do not have a DVD drive, such as a netbook. If you own a Nokia Symbian S60 phone, you will most likely be aware of the fact that it is not possible to install applications on it unless they are signed using a valid certificate. Have you been trying to install applications on your S60 3rd or 5th edition phone but ending up getting a certificate error? At times, this can be really annoying; but here is a smart solution to this problem!
If you own a Nokia Symbian S60 phone, you will most likely be aware of the fact that it is not possible to install applications on it unless they are signed using a valid certificate. Have you been trying to install applications on your S60 3rd or 5th edition phone but ending up getting a certificate error? At times, this can be really annoying; but here is a smart solution to this problem!
